iTrust Summary
The Problem and the Solution
The free flow of information is one of the basic tenets of
liberty. Today, we rely on the Internet to access
information. Currently, our trust in the accessibility of information
over the Internet and the Web depends on benign and unbiased
administration of centralized search engines. Unfortunately,
centralized systems rely on one or a few nodes that can be easily
subverted to censor information.
In this NSF research project, we have developed a distributed and
decentralized publication, search and retrieval system, named iTrust.
Our initial implementation of iTrust, based on the HyperText Transfer
Protocol (HTTP), is most appropriate for desktop or laptop computers
on the Internet. However, today, many people use mobile phones to
organize their activities and, in many countries, mobile phones are
the only computing platform generally available. Consequently, we have
developed a version of iTrust for mobile phones using the Short
Message Service (SMS). To guard against the risk that both the
Internet and the cellular telephony infrastructure are disabled, we
have developed a Wi-Fi Direct version of iTrust for mobile ad-hoc
networks. Mobile phones or tablets enabled with Wi-Fi Direct can share
information directly, without the need for wireless access points or
cellular network connections. Thus, with iTrust, users can decide
which kind of network is most appropriate for their current needs, and
they can share information without reliance on, or interference from,
a third party. Figure 1 illustrates the different kinds of networks
over which iTrust operates.
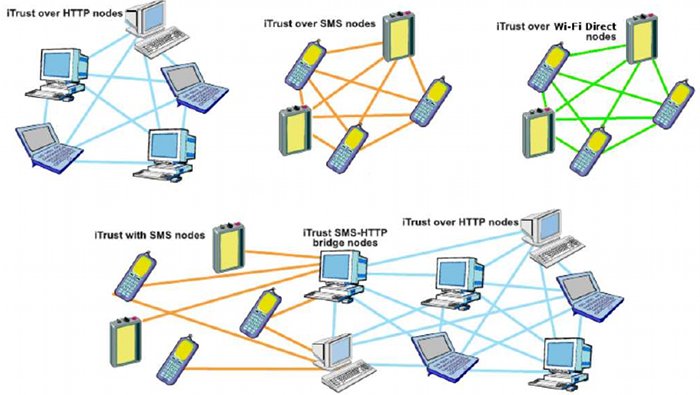
Figure 1. The iTrust networks, showing the iTrust over HTTP nodes, the iTrust over SMS nodes, the iTrust
over Wi-Fi Direct nodes, the iTrust with SMS nodes, and the iTrust SMS-HTTP bridge nodes, publishing,
searching for, and retrieving information.
The Basic Idea of iTrust
The iTrust network is an unstructured network in which all nodes are
equal. Some of the nodes, the source nodes, produce information, and
make that information available to other participating nodes. The
source nodes also produce metadata that describes their information.
A source node distributes the metadata, together with the address of
the information, to a subset of the participating nodes chosen at
random.
Other nodes, the requesting nodes, request and retrieve
information. Such a node generates requests that contain keywords, and
distributes its request to a subset of other participating nodes
chosen at random. Nodes that receive a request compare the keywords in
the request with the metadata they hold. If a node finds a match,
which we call an encounter, the matching node returns the address of
the associated information to the requesting node. The requesting node
then uses the address to retrieve the information from the source
node. Figure 2 illustrates the basic concept of iTrust.
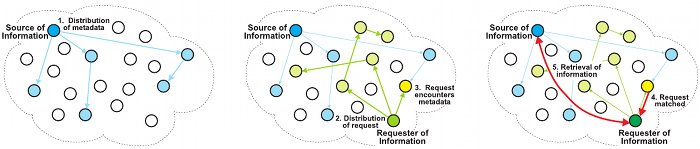
Figure 2. At the left, a source node distributes metadata, describing its information, to randomly selected
nodes in the network. In the middle, a requesting node distributes its request to randomly selected nodes in
the network. One of the nodes has both the metadata and the request and an encounter occurs. At the right,
a node matches the metadata and the request and reports the match to the requester, which then retrieves the
information from the source node.
The Intellectual Merit
The intellectual merit of the iTrust publication, search and retrieval
system lies, in part, in its distributed and decentralized nature, and
its objective to support the sharing of information without fear of
censorship. It also lies in its probabilistic nature and its
distribution of both the metadata and the requests (queries) to
randomly chosen nodes in the network.
The intellectual merit of iTrust also lies in its statistical
algorithms for detecting and defending against malicious nodes in the
iTrust network. Using the chi-squared statistic and the exponential
weighted moving average, the novel statistical detection algorithm
estimates the proportion of subverted or non-operational nodes in the
iTrust network. The novel defensive adaptation algorithm then
increases the number of nodes to which the requests are distributed to
maintain the same probability of a match as when all of the nodes are
operational.
The intellectual merit of iTrust also lies in its adaptive membership
protocol, which exploits the messages that are already being sent to
distribute metadata or requests, thus reducing the need for additional
messages. The novel adaptive membership protocol estimates the
membership churn, i.e., the nodes joining or leaving the membership,
based on the responses that a node receives to its requests. The node
then dynamically adjusts the number of nodes to which it sends
metadata and requests to compensate for the changing membership.
The Broader Impacts
The most significant broader impact of iTrust is societal. The free
flow of information is the primary determinant of a free and
democratic society. The free flow of information discourages small
groups of people from trying to abuse the government, the economy or
the environment for their own personal gain. Many research projects
provide benefits to individuals, but it is rare for a research project
to provide benefits to society as a whole.
More specifically, the benefits of iTrust include the ability to
create mobile ad-hoc networks using Wi-Fi Direct, which can be of
substantial benefit in less developed countries of the
world. Distributed membership algorithms have benefits for many modern
networked computer systems. The ability to detect malicious attacks
indirectly by statistical inference has substantial benefits for many
distributed systems.
Additional information on iTrust can be found in the publications,
presentations, source code and documentation listed below.
Publications
-
Analysis of the Match Probabilities for the iTrust Information Network with Message Forwarding
L. E. Moser and P. M. Melliar-Smith,
Proceedings of the International Conference on Information Networking 2014,
Phuket, Thailand (February 2014), 340--345.
-
Probabilistic Analysis of Message Forwarding
L. E. Moser and P. M. Melliar-Smith,
Proceedings of the IEEE International Conference on Computer Communications and Networks,
Nassau, Bahamas (July-August 2013).
-
The iTrust Local Reputation System for Mobile Ad-Hoc Networks
W. Dai, L. E. Moser, P. M. Melliar-Smith, I. Michel Lombera and Y. T. Chuang,
Proceedings of the 2013 International Conference on Wireless Networks,
Las Vegas, NV (July 2013), 162-168.
-
Mobile Ad-Hoc Search and Retrieval in the iTrust over Wi-Fi Direct Network
I. Michel Lombera, L. E. Moser, P. M. Melliar-Smith and Y. T. Chuang, Proceedings of the Ninth International Conference on Wireless and Mobile Communications, Nice, France (July 2013), 251-258.
Best Paper Award
-
Peer Management for iTrust over Wi-Fi Direct
I. Michel Lombera, L. E. Moser, P. M. Melliar-Smith and Y. T. Chuang,
Proceedings of the 2013 International Symposium on Wireless Personal Multimedia Communications,
Atlantic City, NJ (June 2013).
-
A Distributed Ranking Algorithm for the iTrust Information Search and Retrieval System
B. Peng, L. E. Moser, P. M. Melliar-Smith, Y. T. Chuang and I. Michel Lombera,
Proceedings of the 9th International Conference on Web Information Systems and Technologies,
Aachen, Germany (May 2013), 199-208.
-
Discovering Joining Nodes and Detecting Leaving Nodes in the iTrust Membership Protocol
Y. T. Chuang, P. M. Melliar-Smith, L. E. Moser and I. Michel Lombera,
Proceedings of the 2013 International Conference on Computer Science,
Hong Kong, China (March 2013),189-194.
Best Paper Award
-
Mobile Decentralized Search and Retrieval using SMS and HTTP
I. Michel Lombera, L. E. Moser, P. M. Melliar-Smith and Y. T. Chuang,
ACM Mobile Networks and Applications Journal, vol. 18, no. 1 (February 2013), 22-41.
-
Decentralized Search and Retrieval for Mobile Networks using SMS
I. Michel Lombera, L. E. Moser, P. M. Melliar-Smith and Y. T. Chuang,
Proceedings of the IEEE 8th International Conference on Wireless and Mobile Computing, Networking and Communications,
Barcelona, Spain (October 2012), 134-141.
-
Protecting the iTrust Information Retrieval Network against Malicious Attacks
Y. T. Chuang, I. Michel Lombera, P. M. Melliar-Smith and L. E. Moser,
Journal of Computing Science and Engineering, vol. 6, no. 3 (September 2012), 179-192.
-
A Mobile Peer-to-Peer Search and Retrieval Service for Social Networks
I. Michel Lombera, L. E. Moser, P. M. Melliar-Smith and Y. T. Chuang,
Proceedings of the IEEE 1st International Conference on Mobile Services,
Honolulu, HI (June 2012), 72-79.
-
Declustering the iTrust Search and Retrieval Network to Increase Trustworthiness
C. M. Badger, L. E. Moser, P. M. Melliar-Smith, I. Michel Lombera and Y. T. Chuang,
Proceedings of the 8th International Conference on Web Information Systems and Technologies,
Porto, Portugal (April 2012), 312-322.
-
Detecting and Defending against Malicious Attacks in the iTrust Information Retrieval Network
Y. T. Chuang, I. Michel Lombera, P. M. Melliar-Smith and L. E. Moser,
Proceedings of the 26th International Conference on Information Networking,
Bali, Indonesia (February 2012), 263-268.
Best Paper Award
-
iTrust: Trustworthy Information Publication, Search and Retrieval
P. M. Melliar-Smith, L. E. Moser, I. Michel Lombera and Y. T. Chuang,
Proceedings of the 13th International Conference on Distributed Computing and Networking,
Hong Kong, China (January 2012), Lecture Notes in Computer Science, vol. 7129, Springer, 351-366.
-
Decentralized Mobile Search and Retrieval Using SMS and HTTP to Support Social Change
I. Michel Lombera, Y. T. Chuang, L. E. Moser and P. M. Melliar-Smith,
Proceedings of the 3rd International Conference on Mobile Computing, Applications, and Services,
Los Angeles, CA (October 2011), 152-171.
-
Trustworthy Distributed Search over the Internet
Y. T. Chuang, I. Michel Lombera, L. E. Moser and P. M. Melliar-Smith,
Proceedings of the 2011 International Conference on Internet Computing,
Las Vegas, NV (July 2011), 169-175.
-
Trustworthy Distribution and Retrieval of Information over HTTP and the Internet
I. Michel Lombera, Y. T. Chuang, P. M. Melliar-Smith and L. E. Moser,
Proceedings of the Third International Conference on the Evolving Internet,
Luxembourg City, Luxembourg (June 2011), 7-13.
Dissertations
-
Trustworthy Decentralized Publication, Search, and Retrieval in Heterogeneous Networks
Isaí Michel Lombera, Department of Electrical and Computer Engineering,
University of California, Santa Barbara, June 2013.
-
Trustworthy Distributed Search and Retrieval over the Internet
Yung-Ting Chuang, Department of Electrical and Computer Engineering,
University of California, Santa Barbara, June 2013.
Presentations
-
Analysis of the Match Probabilities for the iTrust Information Network with Message Forwarding
Louise Moser and Michael Melliar-Smith; Phuket, Thailand, February 2014
-
Probabilistic Analysis of Message Forwarding
Louise Moser and Michael Melliar-Smith; July-August 2013, Nassau, Bahamas
-
The iTrust Local Reputation System for Mobile Ad-Hoc Networks
Wei Dai; July 2013, Las Vegas, Nevada
-
Mobile Ad-Hoc Search and Retrieval in the iTrust over Wi-Fi Direct Network
Isaí Michel Lombera; July 2013, Nice, France
-
A Distributed Ranking Algorithm for the iTrust Information Search and Retrieval System
Boyang Peng; May 2013, Aachen, Germany
-
Trustworthy Decentralized Publication, Search and Retrieval in Heterogeneous Networks
Isaí Michel Lombera; May 2013, UC Santa Barbara, Ph.D. Dissertation Defense
-
Trustworthy Distributed Search and Retrieval over the Internet
Yung-Ting Chuang; May 2013, UC Santa Barbara, Ph.D. Dissertation Defense
-
Decentralized Search and Retrieval for Mobile Networks using SMS
Isaí Michel Lombera; October 2012, Barcelona, Spain
-
A Mobile Peer-to-Peer Search and Retrieval Service for Social Networks
Isaí Michel Lombera; June 2012, Honolulu, Hawaii
-
Declustering the iTrust Search and Retrieval Network to Increase Trustworthiness
Christopher Badger; April 2012, Porto, Portugal
-
Detecting and Defending against Malicious Attacks in the iTrust Information Retrieval Network
Yung-Ting Chuang; February 2012, Bali, Indonesia
-
Decentralized Mobile Search and Retrieval Using SMS and HTTP to Support Social Change
Isaí Michel Lombera; October 2011, Santa Monica, California
-
Trustworthy Distributed Search and Retrieval over the Internet
Yung-Ting Chuang; July 2011, Las Vegas, Nevada
-
Trustworthy Distribution and Retrieval of Information over HTTP and the Internet
Isaí Michel Lombera; June 2011, Luxembourg City, Luxembourg
-
Trustworthy Information and Retrieval
Michael Melliar-Smith; April 2011, Marrakech, Morocco
-
Trustworthy Information Distribution and Retrieval
Engineering Insights 2011
Isaí Michel Lombera, Yung-Ting Chuang; April 2011, Santa Barbara, California
Manuals
Code
-
iTrust over HTTP source code
Source code for iTrust over HTTP.
Download and install this code to access the iTrust over HTTP network.
-
iTrust over SMS Android App
An Android app for iTrust over SMS.
Download from your mobile device Web browser, then tap the downloaded file to auto install (must have 'Install from 3rd parties' enabled in Android). If you just want to use the iTrust over SMS network, then all you need is this app.
-
iTrust over SMS source code
Source code for iTrust over SMS.
Download and read to see the source code for iTrust over SMS. You do NOT need this code if you just want to access the iTrust over SMS network (instead, download Android app above).
-
iTrust over Wi-Fi Direct Android Library
An Android library for iTrust over Wi-Fi Direct.
Include this code in your Android apps to gain Wi-Fi Direct capabilities in P2P messaging. You may have to rebuild this code as a library (not project) depending on your Android version.
People
Contacts
{pmms, moser, ytchuang, imichel} @ ece.ucsb.edu



